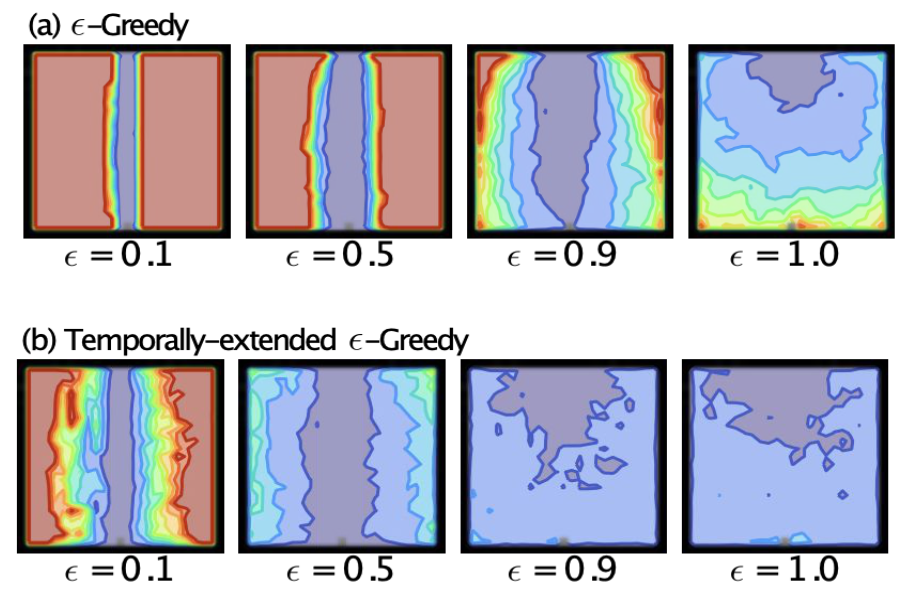
Abstract:
The recent paramount success of the gig economy has introduced new business opportunities in different areas such as food delivery service. However, there are food delivery ride abusers who break the company rule by driving unauthorized vehicles that are not stated in the contract. These abusers are particularly problematic because they break the transportation regulations and unfairly take more orders. However, detecting these abusers are challenging because of lack of labeled datasets and these anomalous abusers do not frequently occur compared to normal riders. Furthermore, sequential patterns of abusing behaviors are not easy to model.In this work, we aim to detect food delivery abusers using unauthorized vehicles, by formulating this problem as a novelty detection over sequential data. We propose the Variational Reward Inference based Novelty Detector (VRIND) using sequential novelty detection using inverse reinforcement learning with variational inference, in which the reward function can learn the behavioral intention of decision-making experts. The reward function is represented by a neural network that is capable of approximating reward distributions by variational reward inference. Using a commercial food delivery trajectory dataset from our company, we demonstrate that our model significantly outperforms over the other baseline methods in identifying novelty (abusers) in sequential data, which can ensure regulatory compliance and provide the fair opportunity to more than 100 thousand delivery riders, serving more than 1.5 million daily transactions in our Baemin food delivery system.